diff options
Diffstat (limited to 'blog/2021-01-07-ufw.org')
| -rw-r--r-- | blog/2021-01-07-ufw.org | 271 |
1 files changed, 144 insertions, 127 deletions
diff --git a/blog/2021-01-07-ufw.org b/blog/2021-01-07-ufw.org index aad5b81..242e296 100644 --- a/blog/2021-01-07-ufw.org +++ b/blog/2021-01-07-ufw.org @@ -1,158 +1,173 @@ -+++ -date = 2021-01-07 -title = "Secure Your Network with the Uncomplicated Firewall" -description = "Learn how to use the UFW, one of the simplest and most widely available firewalls on Linux." -draft = false -+++ - -## Uncomplicated Firewall - -Uncomplicated Firewall, also known as ufw, is a convenient and beginner-friendly -way to enforce OS-level firewall rules. For those who are hosting servers or any -device that is accessible to the world (i.e., by public IP or domain name), it's -critical that a firewall is properly implemented and active. - -Ufw is available by default in all Ubuntu installations after 8.04 LTS. For -other distributions, you can look to install ufw or check if there are -alternative firewalls installed already. There are usually alternatives -available, such as Fedora's `firewall` and the package available on most -distributions: `iptables`. Ufw is considered a beginner-friendly front-end to -iptables. - -[Gufw](https://gufw.org) is available as a graphical user interface (GUI) -application for users who are uncomfortable setting up a firewall through a -terminal. - -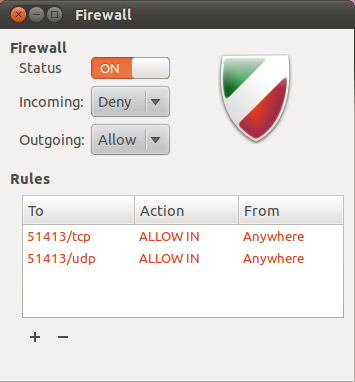 - -## Getting Help - -If you need help figuring out commands, remember that you can run the `--help` -flag to get a list of options. - -```sh +#+title: Secure Your Network with the Uncomplicated Firewall +#+date: 2021-01-07 + +** Uncomplicated Firewall +:PROPERTIES: +:CUSTOM_ID: uncomplicated-firewall +:END: +Uncomplicated Firewall, also known as ufw, is a convenient and +beginner-friendly way to enforce OS-level firewall rules. For those who +are hosting servers or any device that is accessible to the world (i.e., +by public IP or domain name), it's critical that a firewall is properly +implemented and active. + +Ufw is available by default in all Ubuntu installations after 8.04 LTS. +For other distributions, you can look to install ufw or check if there +are alternative firewalls installed already. There are usually +alternatives available, such as Fedora's =firewall= and the package +available on most distributions: =iptables=. Ufw is considered a +beginner-friendly front-end to iptables. + +[[https://gufw.org][Gufw]] is available as a graphical user interface +(GUI) application for users who are uncomfortable setting up a firewall +through a terminal. + +[[https://img.cleberg.net/blog/20210107-secure-your-network-with-the-uncomplicated-firewall/gufw.png]] + +** Getting Help +:PROPERTIES: +:CUSTOM_ID: getting-help +:END: +If you need help figuring out commands, remember that you can run the +=--help= flag to get a list of options. + +#+begin_src sh sudo ufw --help -``` - -## Set Default State - -The proper way to run a firewall is to set a strict default state and slowly -open up ports that you want to allow. This helps prevent anything malicious from -slipping through the cracks. The following command prevents all incoming traffic -(other than the rules we specify later), but you can also set this for outgoing -connections, if necessary. - -```sh +#+end_src + +** Set Default State +:PROPERTIES: +:CUSTOM_ID: set-default-state +:END: +The proper way to run a firewall is to set a strict default state and +slowly open up ports that you want to allow. This helps prevent anything +malicious from slipping through the cracks. The following command +prevents all incoming traffic (other than the rules we specify later), +but you can also set this for outgoing connections, if necessary. + +#+begin_src sh sudo ufw default deny incoming -``` +#+end_src -You should also allow outgoing traffic if you want to allow the device to -communicate back to you or other parties. For example, media servers like Plex -need to be able to send out data related to streaming the media. +You should also allow outgoing traffic if you want to allow the device +to communicate back to you or other parties. For example, media servers +like Plex need to be able to send out data related to streaming the +media. -```sh +#+begin_src sh sudo ufw default allow outgoing -``` - -## Adding Port Rules +#+end_src -Now that we've disabled all incoming traffic by default, we need to open up some -ports (or else no traffic would be able to come in). If you need to be able to -`ssh` into the machine, you'll need to open up port 22. +** Adding Port Rules +:PROPERTIES: +:CUSTOM_ID: adding-port-rules +:END: +Now that we've disabled all incoming traffic by default, we need to open +up some ports (or else no traffic would be able to come in). If you need +to be able to =ssh= into the machine, you'll need to open up port 22. -```sh +#+begin_src sh sudo ufw allow 22 -``` +#+end_src -You can also issue more restrictive rules. The following rule will allow `ssh` -connections only from machines on the local subnet. +You can also issue more restrictive rules. The following rule will allow +=ssh= connections only from machines on the local subnet. -```sh +#+begin_src sh sudo ufw allow proto tcp from 192.168.0.0/24 to any port 22 -``` +#+end_src -If you need to set a rule that isn't tcp, just append your connection type to -the end of the rule. +If you need to set a rule that isn't tcp, just append your connection +type to the end of the rule. -```sh +#+begin_src sh sudo ufw allow 1900/udp -``` - -## Enable ufw +#+end_src +** Enable ufw +:PROPERTIES: +:CUSTOM_ID: enable-ufw +:END: Now that the firewall is configured and ready to go, you can enable the firewall. -```sh +#+begin_src sh sudo ufw enable -``` +#+end_src A restart may be required for the firewall to begin operating. -```sh +#+begin_src sh sudo reboot now -``` +#+end_src -## Checking Status +** Checking Status +:PROPERTIES: +:CUSTOM_ID: checking-status +:END: +Now that the firewall is enabled, let's check and see what the rules +look like. -Now that the firewall is enabled, let's check and see what the rules look like. - -```sh +#+begin_src sh sudo ufw status numbered -``` +#+end_src -```txt +#+begin_src txt Status: active To Action From -- ------ ---- [ 1] 22 ALLOW IN Anywhere [ 2] 22 (v6) ALLOW IN Anywhere (v6) -``` - -## Deleting Rules +#+end_src -If you need to delete a rule, you need to know the number associated with that -rule. -Let's delete the first rule in the table above. -You'll be asked to confirm the deletion as part of this process. +** Deleting Rules +:PROPERTIES: +:CUSTOM_ID: deleting-rules +:END: +If you need to delete a rule, you need to know the number associated +with that rule. Let's delete the first rule in the table above. You'll +be asked to confirm the deletion as part of this process. -```sh +#+begin_src sh sudo ufw delete 1 -``` - -## Managing App Rules - -Luckily, there's a convenient way for installed applications to create files -that ufw can easily implement so that you don't have to search and find which -ports your application requires. To see if your device has any applications with -pre-installed ufw rules, execute the following command: - -```sh +#+end_src + +** Managing App Rules +:PROPERTIES: +:CUSTOM_ID: managing-app-rules +:END: +Luckily, there's a convenient way for installed applications to create +files that ufw can easily implement so that you don't have to search and +find which ports your application requires. To see if your device has +any applications with pre-installed ufw rules, execute the following +command: + +#+begin_src sh sudo ufw app list -``` +#+end_src The results should look something like this: -```txt +#+begin_src txt Available applications: OpenSSH Samba plexmediaserver plexmediaserver-all plexmediaserver-dlna -``` +#+end_src -If you want to get more information on a specific app rule, use the `info` -command. +If you want to get more information on a specific app rule, use the +=info= command. -```sh +#+begin_src sh sudo ufw app info plexmediaserver-dlna -``` +#+end_src You'll get a blurb of info back like this: -```txt +#+begin_src txt Profile: plexmediaserver-dlna Title: Plex Media Server (DLNA) Description: The Plex Media Server (additional DLNA capability only) @@ -160,29 +175,31 @@ Description: The Plex Media Server (additional DLNA capability only) Ports: 1900/udp 32469/tcp -``` +#+end_src -You can add or delete app rules the same way that you'd add or delete specific -port rules. +You can add or delete app rules the same way that you'd add or delete +specific port rules. -```sh +#+begin_src sh sudo ufw allow plexmediaserver-dlna -``` +#+end_src -```sh +#+begin_src sh sudo ufw delete RULE|NUM -``` - -## Creating App Rules +#+end_src -If you'd like to create you own app rule, you'll need to create a file in the -`/etc/ufw/applications.d` directory. Within the file you create, you need to -make sure the content is properly formatted. +** Creating App Rules +:PROPERTIES: +:CUSTOM_ID: creating-app-rules +:END: +If you'd like to create you own app rule, you'll need to create a file +in the =/etc/ufw/applications.d= directory. Within the file you create, +you need to make sure the content is properly formatted. -For example, here are the contents my `plexmediaserver` file, which creates -three distinct app rules for ufw: +For example, here are the contents my =plexmediaserver= file, which +creates three distinct app rules for ufw: -```config +#+begin_src config [plexmediaserver] title=Plex Media Server (Standard) description=The Plex Media Server @@ -197,24 +214,24 @@ ports=1900/udp|32469/tcp title=Plex Media Server (Standard + DLNA) description=The Plex Media Server (with additional DLNA capability) ports=32400/tcp|3005/tcp|5353/udp|8324/tcp|32410:32414/udp|1900/udp|32469/tcp -``` +#+end_src -So, if I wanted to create a custom app rule called "mycustomrule," I'd create a -file and add my content like this: +So, if I wanted to create a custom app rule called "mycustomrule," I'd +create a file and add my content like this: -```sh +#+begin_src sh sudo nano /etc/ufw/applications.d/mycustomrule -``` +#+end_src -```config +#+begin_src config [mycustomrule] title=My Custom Rule description=This is a temporary ufw app rule. ports=88/tcp|9100/udp -``` +#+end_src Then, I would just enable this rule in ufw. -```sh +#+begin_src sh sudo ufw allow mycustomrule -``` +#+end_src |
